
Similar Posts

Visage Review: P.T.’s Spiritual Successor
Story Visage follows a man named Dwayne Anderson, who wakes up to find himself trapped in a house. As Dwayne navigates said house, he is haunted by ghostly apparitions and mysterious events. Despite these factors, Dwayne must progress towards finding the truth behind himself and the house’s past. Visage’s Characters As seen before, Dwayne serves…

How to Use Quadspinner Gaea for Minecraft
Something that has been floating around the Minecraft community for a while, with little documentation is Quadspinner Gaea. While Gaea gets a lot of documentation for game development, there’s not a lot out there to help with Minecraft, which is something that I believe could be fixed. Gaea is a very complex engine, but I…

How To Optimize Minecraft for M1 (Java Edition)
I recently purchased the MacBook Pro with Apple Silicon. However, most apps still are not yet optimized. One of the main apps I care about performing well is Minecraft. However, I have finally figured how to optimize Minecraft for M1 with the MultiMC launcher’s help. IMPORTANT NOTE: This tutorial is for 1.16.5 and below. For…

The Poor Man’s Guide to Making a Supercomputer
How to Make a Personal Supercomputer So, I did this myself a few months ago and it was incredibly difficult. It was difficult mainly because the websites that I could find on the matter were very vague about how to do it. Also, they didn’t make it easy for people who didn’t have a ton…

How to Have a Live Dynamic Map of Your Minecraft Server
How to Install Dynmap on Your Minecraft Server My friend showed me a truly interesting thing that he created with his Minecraft server. He had created a live map that showed the locations of every player as well as two-dimensional and three-dimensional versions of the map of the server. In this tutorial, I will show…
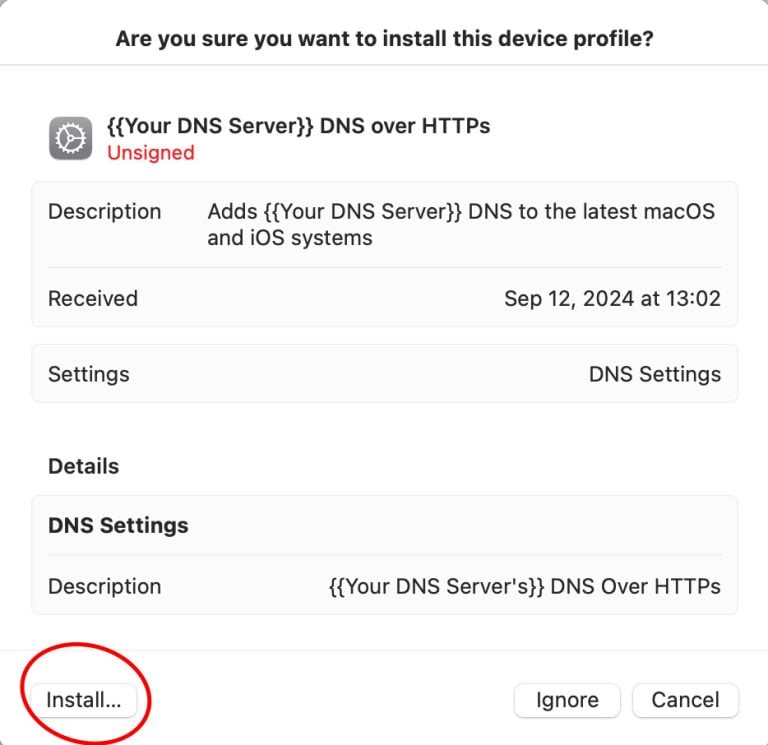
How to Activate DNS over HTTPS on Mac and iOS
DNS over HTTPS (DoH) and DNS over TLS (DoT) on Mac and iOS are giant steps forward regarding privacy, security, and corporate system management. Using traditional DNS protocols allowed malicious users who had gained control of networks to either regulate traffic or redirect traffic from legitimate websites to malicious websites. Apple has created DoH and…