How to Easily Live an Untrackable Life
The year is 2022. The world’s most popular browser is Google Chrome. The world’s most popular Search Engine is Google. However, what if I told you, yes you, the viewer, that other options exist and they’re not hard to figure out either. In fact, living an untrackable life is extremely easy. Depending on your current setup and what you may have done in the past to protect your privacy, it may be easier or harder. You don’t have to be using Linux to live off the grid. No, You don’t have to use Tor or anything that tries to throw an AK-47 at a shotgun-sized problem. You don’t even need a VPN!
The Corporate Understanding
I’m going to get into fairly basic economics for a minute, so bear with me. To understand companies that track people, you must understand supply and demand. Because being spied on, like anything else, has its supply and demand. Contrary to popular belief, supply and demand are curves on a graph, not specific scalar values. The demand curve on one end is the users who want ads that are most relevant to them and don’t care about privacy at all. On the other end of the curve is the die-hard tinfoil hatters.
The supply curve recognizes the point of view of companies. One side of the supply curve is no spy at all. On the other side of the curve is pouring out so much money to get every possible user imaginable into tracking that the company goes bankrupt.
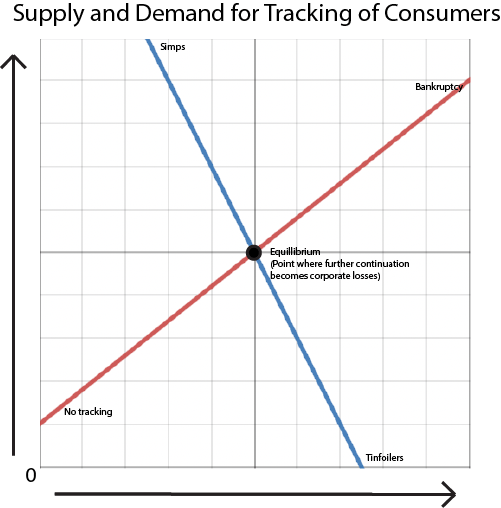
If you see where this is getting at, it is not economically viable to track beyond a certain point. Now, the chart I have given is more of a simplification. In reality, the curves are more complex and will appear logarithmic. Also, notice that I did not give specific dollar amounts. The point of this article is to get you not to become a tinfoiler but instead to put you beyond companies such as Google and Microsoft’s equilibrium. That way, it will no longer be financially viable to spend the R&D effort and put forth other costs to create ways of tracking you.
At the end of the day, the end goal is to turn a profit. Anything beyond equilibrium will not make you a profit.
Privacy Myth vs Reality
Firstly, I would encourage you to read another article critically discussing VPNs: The Truth About IP Addresses.
Regarding VPNs
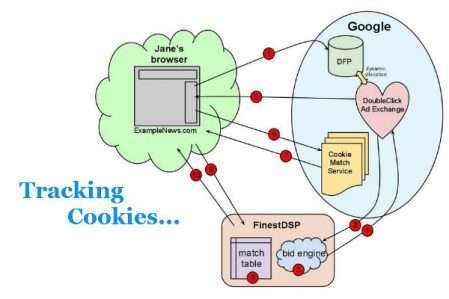
If you do not have time to read, here’s the takeaway. VPNs won’t save you from tracking companies such as Google and Microsoft. They are far more useful for getting around firewalls and if you believe whoever provides your internet is spying on you. They are also useful if you wish to circumvent any potential IP bans, including country filters. As that market is a smaller market that is often looked down upon by society (e.g. kids in schools getting around filters), VPNs often advertise that they will protect your privacy.
The issue with this is that while they advertise privacy protection, people actually looking for genuine privacy protection may be led down the wrong path. The primary way that Google and other trackers operate is not through your IP address but through cookies stored on your browser. Those cookies will be recognized regardless of your IP, and Google will always see them as you.
Don’t get me wrong; Google likely does use your IP address in some capacity. However, it can often be limited in effectiveness to do so considering home IPs change, anyone living under the same roof shares the same IP, and if you live in a college or university dorm, or are at a coffee shop or anywhere other than home, IP addresses on their own are a rather inaccurate method of tracking that may cue Google in part to who you are but must be combined with other variables.
Regarding TOR
TOR is an option that does exist. However, as I’ve said before, TOR is a machine gun used to solve a shotgun-sized problem. While TOR has made efforts to not lure their users into a false sense of security, it is still possible to get one.
Check out my article The Truth About the Dark Web to see more information on TOR.
However, I think the primary problem with TOR is the ease of use. TOR is a hassle to use. It’s made to protect you against the government, not against companies. It’s extremely slow, and if you decide to use TOR to solve your problems, chances are you will be returning to Chrome in no time.

All of this being said, TOR is amazing at protecting your privacy against outside forces. However, the outside forces are not the ones you need to be exclusively worried about. If there is an app on your computer, or G-d forbid, your operating system itself that is phoning home the websites you visit, TOR did nothing. Also, the second you log into your Gmail account, Google knows you’re a TOR user.
Apple and TOR
Believe it or not, Apple has its very own version of TOR. It requires a small monthly iCloud subscription, but it’s not that much. iCloud Private Relay runs entirely off of Apple’s own servers, so there’s no worrying about using some random guy’s basement computer. However, it employs the same technology that TOR does. It goes through one server, which only sees your IP, and sends the request to another server that only sees what website is being accessed. Right now, it only works on Safari, but if you’re using an Apple device, it does exist, and as far as I can tell, when I have it on, I see zero changes in site speed than when I have it off. This is because, unlike TOR, iCloud Private Relay attempts to only use servers in your general area.
Regarding Linux
It’s spouted by many of the popular tech people that if you want privacy, Linux is the way to go. And, while, yes, Linux does a very good job at preventing the Operating System from phoning home, your apps may not be doing likewise, and if they don’t, Linux does nothing to protect against that. It’s a common joke among the community to “Use Linux and then Install Google Chrome Immediately Afterwards.”
The fact is that Linux does absolutely nothing to protect your privacy. There is zero app sandboxing whatsoever. While many distributions may include Snap or Flatpak, which are two marketplaces that allow for sandboxing, the simple fact is that any app that wishes to spy will merely not provide a snap or flatpak version of itself, and users will not think twice before installing it.
Complex Talk About Permissions
An app that wishes to harm your computer may need to have write access to certain things, but any app that wishes to spy neither requires root nor requires to write permissions, and basically, every file on your system is given read permission. While many distributions fix this issue, Linux on its own allows any program, root or not, to have full read access to the entire system memory. Your discord tokens, your sessions on various websites, and all of this secure data can be read and leaked by any application, with or without root.
Besides that, the data that should be kept private is not the data that is kept in different locations on the system. It’s the data that’s stored in your home directory. Any program that you run has full access to everything within that directory. Furthermore, by default, Linux allows anyone who wishes to read anyone’s home directory full read access. This can’t be changed unless you manually change it yourself. You will also need to change your umask to do likewise with other files in the future. This means that in both a single-user and multi-user way of thinking, Linux is terrible.
Many people ask “Why hasn’t Linux made it to the desktop in big-time yet, when it has for every other use of a computer?”. Linux on the desktop is barely any more secure than MS-DOS, which had zero security as a base whatsoever. The ability to modify the file structure and change the philosophy slightly is there for Linux. The only thing in the way is that every distro in existence has failed at doing so.
Final Note Regarding Background Processes
The final nail in the coffin regarding Linux’s security on the desktop is something Mac and Windows both have in some form or another, but Linux lacks. On Windows, at the bottom-right of the screen, there is a system tray. Any application that wishes to run in the background is kept in that tray. On Mac, they are lined up as menus on the top right of the screen. Those are the apps that spy. Not all of them do spy, and most have a legitimate reason to be there. But, if there is one that is up there and shouldn’t be, it is easy to identify.
On Mac and Windows, rules exist that enable those apps to do certain but not all root-level activities. Different apps may request different things. However, let’s look at Linux’s horrible solution from the 1970’s. What Linux has is called a daemon. Daemons were originally created as servers. Apache HTTP is often called “httpd” or “HTTP daemon”. Daemons are started as the computer powers on. They are initially given full root access and may choose to fully or partially change themselves to an unprivileged user in the interest of security.

However, from a desktop perspective, Daemons suck. Consider the fact that you, the user, give root access to every app at install time. While Windows requires administrator access, they make it a little more complex. In the case of Mac, you just drag your apps into the Applications folder, and you’re done. Any application could potentially make itself a daemon at install time. Daemons are invisible to the desktop and can run in the background without any visible sign to the user unless the user opens up the full list of tasks. Applications can not only spy on the user this way but can also receive full system access and spy on every user.
Regarding Firefox
Many people regard firefox as the most privacy-protecting major modern browser. And Firefox is good at protecting your privacy. However, in everything that Firefox does, Safari does better. If you are not using an Apple device, you really don’t have a choice. However, I would urge you that if you are intending on using Firefox, to instead consider something based on Firefox, such as Librewolf: https://librewolf.net.
First of all, Firefox isn’t entirely secure by default. There is telemetry that is sent to Mozilla, and given the foundation’s history, should be disabled. Mozilla, while in the past may have been amazing, they have sold out a good bit recently. You can do more research on the matter if you wish, but let’s just say they’re not quite as non-profit as they used to be.
Firefox from a Non-Privacy Perspective
If you’re reading this article, while privacy is on your mind, you likely wish to have the most privacy with little sacrifice. However, you are making a pretty significant sacrifice by using Firefox, as opposed to Safari or other Chromium-based browsers. The time of writing this article is 2022, and the link below will take you to a list analyzing the speed of browsers taken in April 2022: Chrome, Edge, Firefox, Opera, or Safari: Which Browser Is Best?, PCMag
There are three benchmarks that were included. HTML5Test measures compliance with existing web standards. Safari bites the bucket more than anyone on this, although the cause may be because some standards may not be complied with or may be done differently to protect the user’s privacy. The second benchmark is called JetStream 2. JS2 measures the actual speed in which the browser renders the pages. Finally, there’s a memory use benchmark, which looks at how much memory different browsers use.
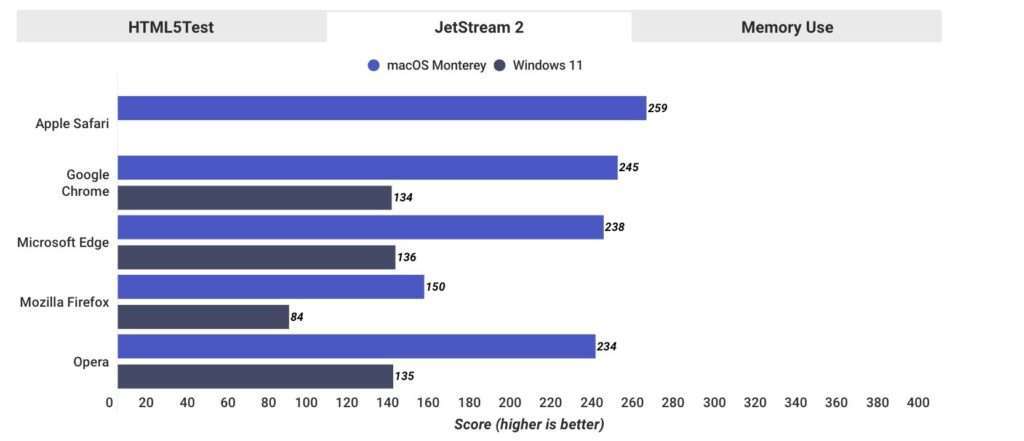
As you can see, Safari comes in well beyond all other browsers in terms of speed. Firefox does the worst out of everything on the list, unfortunately. It is significantly slower than Chromium-based alternatives.
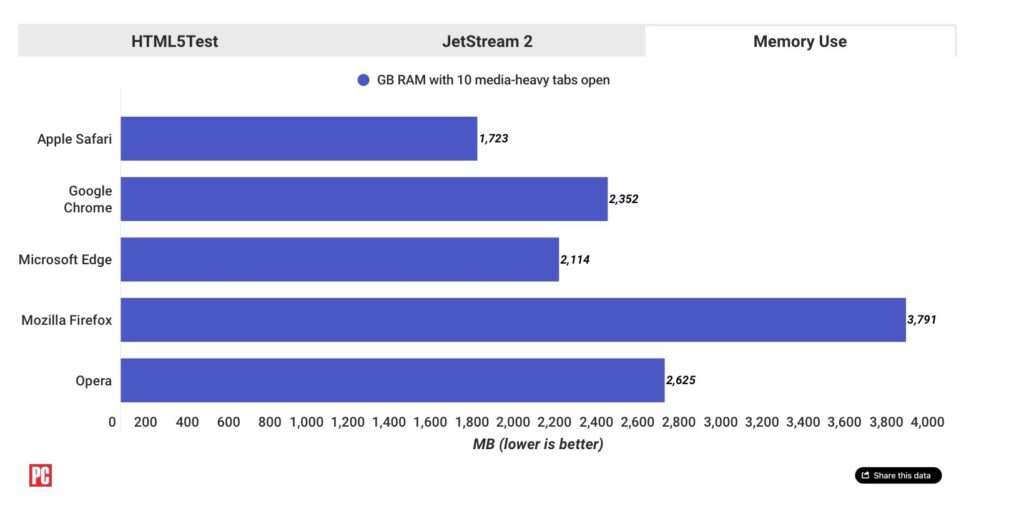
As you can see here, although Google Chrome is commonly famous for using a ton of memory, it actually isn’t that bad. Firefox uses an inordinate amount of RAM, while Safari is incredibly lightweight and far faster.
Finally, the Reality
Now, we’re past the myths, so we should talk about what you should do. The key is that you want your computer to be secured from prying eyes on both the foundation level and any apps that may be running on your computer. And, thankfully, that isn’t that hard.
Your Phone Must be Just as Secure as your PC
One of the most common mistakes people make is they do everything they possibly can to keep their computers secure, while they neglect their phones entirely. However, your phone is the thing that’s always looking at your location. You leave your computer at home. Your phone is also where you do likely the majority of your searches you may not want Google to know about. The fact is that your phone’s search history is going to be far more valuable than your computer’s. Your phone is where you search things up that pertain to real life. Your computer is where you do searches that pertain to video games.
One of the reasons that this may be is your phone’s settings may seem more difficult to sift through than your computer. When people get their computers, they often immediately configure everything for their liking. However, with a phone, your previous phone might have broken. Or, something else might have happened, and the user’s initial priority is to see what conversations happened while they were gone and get everything working before they fully configure the operating system.
Android-Specific Advice
It is possible to recover from this though, even on Android. If you’re on Android, one of the first steps to do is remove the Google widget. Androids have a Google widget. That widget circumvents the use of an actual browser. Actual browsers let you configure whatever non-Google search engine may be preferred and better protect your privacy. You may not be able to uninstall it, but all you really need to do is get it off the screen, so using it is not convenient.
After doing that, sift through the settings. This may surprise you, but Google made a good bit of privacy options. You will never be safe from tracking that comes from apps installed on your phone, but one good way to know how certain apps might track you is to go to the website of the App Store and just look at Apple’s list of what the app is doing on iPhones. Some apps that exclusively exist on Android are likely there to spy on you. If you look at an App that exists in both stores, and you see that it’s free on Google Play on the App Store, when you look at Apple’s privacy summary, it looks pretty good, but then you see that it costs money on Apple, it’s probably spying on you.
Also, this should go without saying, but consider using the DuckDuckGo browser or other privacy-focused browsers on your phone instead of Chrome. Android does actually allow you to set a default browser.
iOS-Specific
iOS protects your privacy a lot better than Android does. However, you still should give your settings a look. Obviously, use Safari and don’t install Chrome or something onto your iPhone. However, it is highly advisable to look through each of the settings for every app you install.
Also, watch the location icon on the top right. If it’s hollow, your location isn’t currently being scanned, but a running app possesses the capability to do so. Assuming it is full, an app in the background is obtaining your location. If there are no apps other than the current one open, it is probably something like Find My or another Apple service, which you can either disable or keep open.
For Both OSes
Moreover, this is going to be a big talking point later on, but uninstall any and all apps you don’t use. If it doesn’t need to be there, it shouldn’t be. Just uninstall it.
Furthermore, if swiping up and quitting apps as soon as you no longer need them is not an OCD and a habit for you, make it one. Those apps are still running. If they’re running, they could be spying. This includes closing browser tabs, as mobile browsers do not remove tabs when quit, and tens of websites from weeks or months ago could be open without your knowledge. Do this not only for privacy but also to extend battery life.
App Use Advice
As I’ve said previously, ideally the best browser you can use is Safari, for both privacy and speed. However, with knowledge of the speed issues with Firefox in mind, I would recommend DeGoogled Chromium instead for anyone without an Apple device. I highly recommend using an Apple device for privacy. And as I’ve said before, Apple has nothing to gain from spying on you. It’s not their business model.

Additionally, same as with phones, go through every part of the settings and configure everything on your computer to maximize privacy. And then, ensure you’re removing everything off of your computer.
However, there are a number of reasons why someone may not want an Apple device. They’re still far behind Windows in gaming. Also, while Apple Silicon’s graphics has gotten far better with the advent of the more powerful Apple processors, the graphics units continue to be optimized more for video rendering and arts than gaming. Also, many game devs, especially valve, would make games for Linux sooner than Mac.
The Case for Windows
Previously I mentioned that Linux does nothing to protect you from the apps you install on your computer. From a privacy point of view, if the primary problem is not your OS spying on you but instead the apps, I would highly recommend remaining on Windows. And while yes, there is no option to completely turn off telemetry altogether at setup, it is, in fact possible to update the registry and/or Group Policies manually to remove telemetry entirely: How to Disable Telemetry on Windows 10 and 11, MakeUseOf.
Edge is a lot faster than Chrome, but Edge sends a lot of data home (far more than Chrome). Therefore, it’s advisable to use DeGoogled Chromium.
Tracker Prevention
Regardless of whether your browser has built-in or not, I recommend installing DuckDuckGo Privacy Essentials. This will change your search engine to DuckDuckGo and block any trackers. Also, just for good measure, I would advise you to install it on both Safari and Firefox as well. DuckDuckGo has a far more complete list of trackers. If DuckDuckGo Privacy Essentials does not exist, I would recommend uBlock Origin. This is also a very good ad blocker, although I personally opt not to block ads. I believe website owners should be entitled to a certain amount of money to make a living. The important thing is making sure the ads don’t follow you around not them not showing altogether.
In my opinion, DuckDuckGo is simply the best option for search engines. One issue, though, is that it does use Bing. Because of disputes we’ve had with Microsoft in the past, Info Toast is not on Bing. So, in the future, if you’re searching for something that Info Toast wrote or possibly something that we’d be likely to write about, I would encourage you to use Google. After all, we don’t tend to write about the stuff people are often self-conscious about anyways. DuckDuckGo has bangs, which enable you to search specific sites or be redirected to sites. To use Google, just type !g <search>.
Normalcy
One of the most used but least discussed methods that trackers use is device fingerprinting. This involves what hardware your device uses, the OS version, the browser being used, the screen size, and other things. It is possible to fake your user agent, although some browsers make it more difficult to do so than others. Tor always opens its windows the exact same size to prevent javascript from making assumptions about screen size.

In general, if you’re willing to spend at least a little money, make your computer as “normal” as possible. Building your own PC might be a good idea for performance and money-saving. However, it also means that nobody else in the world likely has the same hardware. As far as privacy is concerned, you should buy the most purchased prebuilt PCs and screens around. If you purchase a Macbook, you will be among the millions of other people who have that exact Macbook. A commonly purchased Windows laptop such as a Thinkpad is also a good choice. Laptops are also better than desktops as with desktops you have to buy your own screen.
This may be one of a few reasons that technically-savvy people have to buy what everyone else is buying.
Conclusion
In this guide, I didn’t set a path for you but instead gave you loose guidelines on what to do. I also displayed what pitfalls and false senses of security exist. The way you choose to follow this guide is entirely up to you. I would advise that you generally stay within the guidelines I’ve given you.





Why would you recommend Windows when you can change read permissions on Linux? Windows has built in tracking that is very hard to disable. On Linux, you can remove any program you want easily, and if you want protection from apps spying on you, you can change file permissions. If you’re worried about Daemons, simply don’t install Daemons that you don’t trust and always read the install script for programs.
Also, I would say use Searx, not DuckDuckGo. Although DuckDuckGo is better for privacy than Google.
apple’s iCloud relay is nothing like tor. It’s all owned by one mega corporation which allows for corruption easily. Compared to thousands of people around the globe which is near impossible to corrupt due to it being thousands of different servers and server owners.
I never intended to say that Tor is less secure than iCloud Private Relay. Tor will always be more secure, but this article is about the moderate view on things, and how to be reasonably private without using an AK-47 for a pistol-sized problem. iCloud Private Relay uses similar technology to Tor, and while it is all owned by the same company, so is literally every VPN provider other than Tor. Apple, while they haven’t always been perfect, have a track record at being slightly better than every other tech company.